Getting to know DMARC in Plain English
What is DMARC?
We often get a lot of spam emails on our inbox and have you ever notice an email claiming to be from a company and it is obvious it wasn’t? This is phishing activity that is the result of domain spoofing from someone trying to phish personal data of the recipients. Email infrastructure isn’t perfect and can still be intentionally exploited by anyone. In order to protect your company name or brand in the form of your own domain from being spoofed you need to consider email security authentication. This what DMARC is for.
DMARC–Domain-based Message Authentication, Reporting & Conformance is the latest advance in email authentication. DMARC was created to tell a participating receiving server what to do with a message that fails both SPF(Sender Policy Framework) and DKIM(Domain Keys Identified Mail) validation. In other words, what to do if a message claims to be from you, but isn’t.
Deploying DMARC for your email systems is a powerful way to help prevent malicious entities from potentially spoofing or otherwise tarnishing your good name. But DMARC isn’t for everyone–if you own a small domain, you’re probably ok without it. If you have ever had problems with phishing in the past, or have a business that is financial-oriented in nature, it might be right for you.
How it works: DMARC’s alignment feature prevents spoofing of the “header from” address by:
- Matching the “header from” domain name with the “envelope from” domain name used during an SPF check, and
- Matching the “header from” domain name with the “d= domain name” in the DKIM signature.
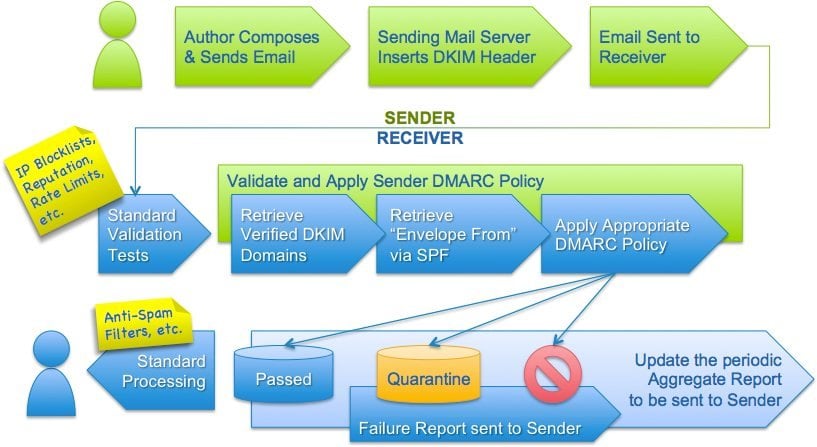
To pass DMARC, a message must pass SPF authentication and SPF alignment and/or DKIM authentication and DKIM alignment. A message will fail DMARC if the message fails both (1) SPF or SPF alignment and (2) DKIM or DKIM alignment.
DMARC allows senders to instruct email providers on how to handle unauthenticated mail via a DMARC policy, removing any guesswork on how they should handle messages that fail DMARC authentication. Senders can either
- Monitor all mail, to understand their brand’s email authentication ecosystem, and ensure legitimate mail is authenticating properly without interfering with the delivery of messages that fail DMARC.
- Quarantine messages that fail DMARC by moving it to the spam folder
- Reject messages that fail DMARC by preventing delivery.
NOTE: Mailbox providers can also send regular DMARC aggregate and forensic reports back to senders, giving them visibility into what messages are authenticating, what messages are not, and why.
DMARC is now a widely deployed technology that can make the “header from” address trustworthy. This helps protect customers and the brand; it discourages cyber-criminals who are less likely to go after a brand with a DMARC record.
If you want to know more or need help with implementing these technologies contact Team Discovery.



